Our Approach
Approach we follow
01

Planning & Reconnaissance
We plan the execution...
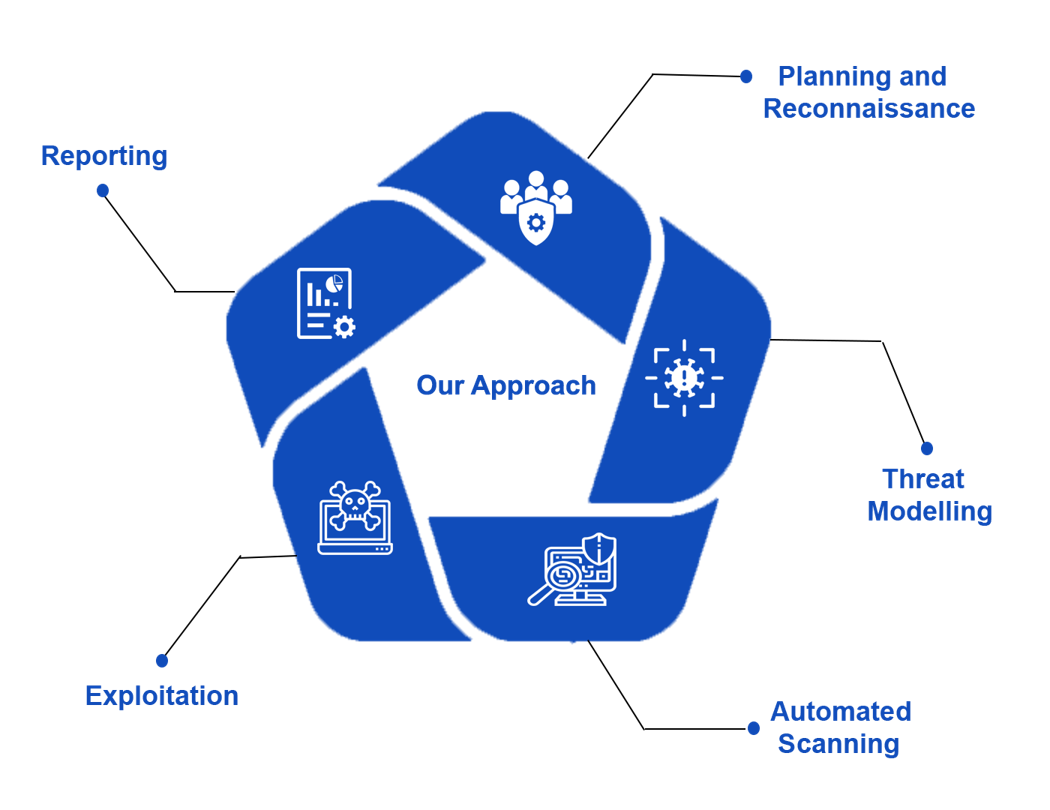
02

Threat Modeling
...
Automated Scanning
...
03

04

Exploitation
...
Reporting
...
05
